In today’s world, the ability to quickly create value from different types of data increasingly provides businesses with a competitive edge. An excellent example of this is how responsive, personalized and portable a food delivery app might be. But how does a business become data-driven? The easiest way for businesses to generate this type of value […]
For any large government agency, managing cloud migrations can be fraught with risk, complexity, and hidden costs. However, the U.S. Department of Agriculture (USDA) was able to overcome these obstacles and establish winning implementations in the public, or commercial, cloud. How? In this first of our two-part blog, we offer background on the USDA, the […]
Introduction At some point in their cloud journey, most organizations hit a major obstacle. After experimenting with a workload or two, organizations begin to scale their cloud investment and estate. It is only then that executives realize they have a problem: their teams lack the skills, tools, and processes they need to track, manage, and […]
Cloud technologies are now firmly established as the norm for enterprise IT. In fact, most organizations are now tying digital transformation strategies firmly to a cloud-first approach. According to Gartner, growth in enterprise IT spending for cloud-based offerings will be faster than non-cloud spending through 2022—what they term the “cloud shift”. And the drive is not just because of […]
The value of DevOps has continued to increase as digital transformation and cloud adoption initiatives have become mainstream in almost all sectors of the economy. OpsRamp reports that nearly three-quarters of survey respondents expect to either accelerate or maintain digital transformation initiatives and projects. Embracing DevOps practices is the only way to accelerate these activities through a seamless management of development […]
According to Forrester, as of the end of 2017, 50% of organizations were actively implementing and expanding their DevOps services. 13% of respondents have already made use of DevOps while 36% plan to adopt it in the future. And that’s not surprising. The increased productivity and performance that come with this approach bring companies more income […]
In this blog post we’re giving you an overview of the most recent DevOps reports from Puppet, DORA, and the DevOps Institute. We will highlight important information from each report below. Then, read on for the steps successful organizations can take in adopting DevOps. Puppet’s State of DevOps Every year, Puppet reports on the State of DevOps. […]
With a variety of philosophies and methodologies adopted in the tech world, figuring out what each one encompasses can be confusing. If you focus closer on an entire culture shift, such as DevOps, even that type of approach comes with as many different definitions as there are developers. Going further into DevOps are ideologies like SecOps […]
Whether you’re an individual or a small business, blogging is the ideal way to spread your ideas, share information, and build a community around your brand. By dedicating time and resources to building a website and a blog, you create a platform where billions of Internet users can directly interact with your content. When blogs develop a […]
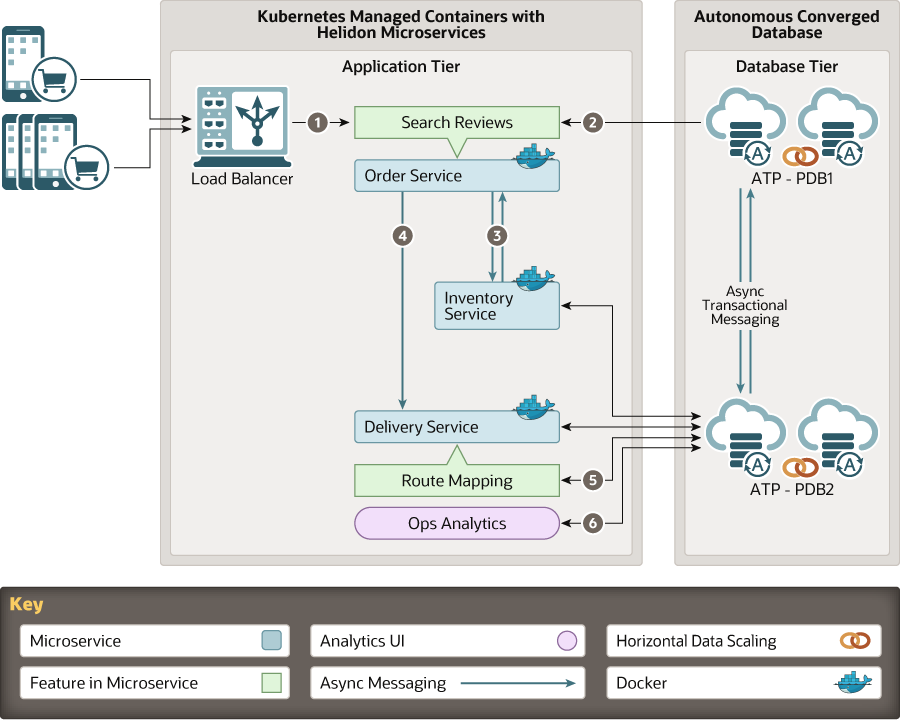
Oracle Sharding is now available in Oracle Cloud with Oracle Database Cloud Service as well as Kubernetes and Docker containers (OKE). Oracle Sharding enables hyperscale, globally distributed, converged databases. It supports applications that require linear scalability, elasticity, fault isolation and geographic distribution of data for data sovereignty. It does so by distributing chunks of a data set across independent […]