IoT Compliance: How to hedge against security breaches
A 2018 DigiCert survey revealed that 100% of companies struggling to implement IoT security compliances had faced at least one IoT security incident. Fast forward to 2020, IoT adoption has increased manifold owing to social distancing and lockdown norms during the ongoing COVID-19 pandemic. This has led to even more vulnerabilities and IoT security breaches.
According to a new survey released by iomart in April 2020, if a data breach of 10-99 million records in tech sector remains undetected for 246 days, it could result in an estimated loss of USD 42.9 billion to the top 10 tech companies on FTSE 100 and Nasdaq 100. The straightforward answer to mitigating these losses is implementing IoT compliance by design to address IoT security concerns.
Who should be compliant?
There are many components in the whole IoT system, and all of them to be compliant to ensure overall compliance:
- People
- Processes
- Devices
- Technologies/software
Educating teams about importance of IoT compliance
IoT teams must be aware of existing IoT compliances and how they can implement it in their products from the word go. In fact, it is advisable to have at least one stakeholder on board the IoT project management team who is invested in ensuring that IoT compliances are met. This is essential to ensure that project outcomes match the overall organizational business goals. As we will discuss later, inability to meet IoT security compliance requirements can result in serious data breaches and loss of both revenue and reputation.
Establishing IoT compliance processes
The first step towards IoT compliance must be establishing processes to comply with industry standards and protocols as well as government regulations. IoT systems generate huge amount of personal data. Governments all over the world are waking up to the potential devastation caused by security breaches in data generated by IoT system. They are rolling out regulatory guidelines for companies selling IoT products – hardware or software – to follow.
For instance, IoT security guidelines issued by the UK in 2019 shifted the onus of data security on company selling the IoT product rather than the users themselves. IoT system compliance processed also depends upon the industry for which the product or service is being developed. Some industries like BFSI and healthcare are highly regulated. The IoT system operating in these domains must be compliant with all the industry-specific regulations as well as guidelines provided by industry governing bodies.
In BFSI industry, eventually it’s the money, be it of an organization or government or the common people, that is at stake. In healthcare industry, lives of patients are in line. Hence these industries have governing bodies to ensure that businesses in its domain work ethically and effectively. Therefore it follows that any IoT system operating in these industries must adhere to the rules followed by other businesses.
Compliant devices
The widespread adoption of IoT has been made possible by availability of cheap IoT devices and sensors over the past couple of years. However, the reduction in prices has come at the cost of reduced security. Hardware security must be a part of the firmware itself. But implementing this has largely been left to the manufacturers, who obviously cut corners to keep the prices under control. So, it has now become the responsibility of IoT product developers and IoT consultants to ensure that the devices being used by their clients are IoT security compliant.
IoT ecosystem comprises IoT devices, edge devices, networking infrastructure for connectivity and Cloud Computing infrastructure. Any IoT manager must be aware of each of the devices and infrastructure elements making up the IoT ecosystem. Making an exhaustive list of all the hardware components helps in keeping track of how compliant each of them is. Because compliance must percolate to the most atomic level to ensure end to end compliance.
The compliance required for IoT devices depends upon not only the technology it uses but also the country or region where it will be used. For instance, any radio frequency (RF) device must be authorized for use by the Federal Communications Commission (FCC). In fact, any RF device being imported to the US must be FCC compliant. IoT project managers must gain knowledge about localized compliance requirement for the IoT devices being used.
Adopting technologies that are IoT compliant
Once the devices and their firmware are compliant, what remains is the infrastructure for network connectivity. Implementing compliant Technologies for connectivity is crucial to data security. IT developers often overlook compliance issues in connecting the IoT devices to the network because they are used to devices that are compliant with Internet connectivity. However, IoT connectivity is a different ballgame altogether because it consists of low-power devices, Wi-Fi enabled devices, short range devices, Bluetooth devices, etc.
Many IoT compliance standards have been developed which include the following:
- IEEE 802.11ah — As the name suggests comedies protocol is a part of IEEE 802.11 suite of wireless protocols. It is a low energy Wireless networking protocol to extend the connectivity range for Wi-Fi networks.
- Bluetooth low energy — It is a wireless personal area network technology developed by the Bluetooth Special Interest Group. This protocol is used for applications in healthcare, home entertainment, fitness and security systems.
- Zigbee— It is an IEEE 802.3 15.4 based wireless protocol for low power and low bandwidth devices used in devices that are a part of healthcare, home or personal networks.
- Z-wave — It is again a wireless, low power networking protocol developed for home automation systems.
Ideally, these protocols must be embedded as firmware in the IoT devices. And IoT compliance boils down to choosing the right devices. But things are rarely as simple as that. As discussed earlier, many devices do not have the necessary protocols built into it. It’s responsibility of the development team to ensure compliance in the devices they select.
Why IoT compliance is essential
Securing information systems and data associated with it is essential. This data may be generated by the system or needed by the system for its functioning. Whatever the type of data, there is complete agreement among all stakeholders that it must be kept secure. Insecure IoT devices pose a serious threat to the CIA information security model as they can act as the vulnerable gateway to the whole information system.
Confidentiality, Integrity and Availability are the three components of the CIA or AIC (to avoid confusion with the US intelligence agency!!) triad. The triad is used to design policies for information security within an organization. IoT systems must not compromise the CIA or AIC triad.
Whether the IoT devices you are talking about is within your organization or installed at a client’s site, they all patch into a common network that can easily be compromised if any of the IoT devices are insecure. In fact, a smart light bulb or camera connected to the internet is a low hanging fruit for hackers searching for ways to break into a network. As someone invested in ensuring IoT compliance, you must be aware of these three most crucial components of information security that IoT systems must not compromise:
Confidentiality
It is a set of rules that ensures data privacy. Confidentiality guidelines ensure that information is accessed only by the authorized people and not the wrong ones. Data is usually categorized according to its sensitivity or impact caused in case it is hacked. Privacy measures are then implemented according to the importance of these categories.
Encryption, passwords, two factor authentication and biometric verification are some of the most commonly used methods to maintain data confidentiality. Hardware security measures like using air-gapped computers or disconnected storage devices may also be used if the data is highly sensitive.
Integrity
Integrity rules ensure that consistent, accurate and trustworthy data is maintained through its entire life cycle. Data must not be modified during transmission or storage. The first step in ensuring data integrity is restricting access only to authorized people for making changes; everyone should not be able to update it.
File permissions, user access controls, checksum and backups are some of the ways in which data integrity is maintained. Periodic backups are necessary to restore data that has been altered unknowingly or lost in ransomware attack.
Availability
Correct data must be available to the authorized users whenever required. It is made possible by keeping all hardware infrastructure maintained and updated. Both hardware and software must be upgraded whenever possible. Maintaining adequate bandwidth and preventing network bottlenecks is an important aspect of 24/7 availability. Multiple backups of data must be kept so that if one server fails, another is ready to fulfil the users’ demands.
IoT security incidents depend on available IoT security expertise
The IoT security incidents faced by any organization is contingent on the organization’s access to IoT security expertise. The DigiCert survey found that the number of security incidents is inversely proportional to IoT security expertise. For purposes of compiling the survey findings, the surveyed companies were divided into three tiers:
Top tier — Enterprising Enterprises having fewer problems because of expertise in mitigating specific aspects of IoT security
Middle tier – Enterprises having problems but also demonstrating some degree of expertise in in implementing IoT security successfully.
Bottom tier – Enterprises having more problems because of lack of IoT security expertise
Interestingly, the IoT security issues faced by top tier and bottom tier enterprises were markedly different, as shown in the table here.
| Top-tier Enterprises | Bottom tier Enterprises |
| Encrypting sensitive data | Monetary damages |
| Ensuring Data integrity during data transmission | Lost productivity |
| Scaling up security measures | Legal / compliance penalties |
| Securing updates delivery | Lost reputation |
| Securing software-based encryption key storage | Diminishing stock prices |
How to ensure IoT compliance
There are four basic steps that need to be taken to ensure IoT compliance:
- Create a compliance checklist
- Analyze risk based on the environment in which the IoT product or service would operate
- Conduct tests to ensure all items on the compliance checklist is ticked off
- Perform periodic audits to ensure continued compliance
However, devil lies in details. It’s the work required to complete all these four steps that need all your resources.
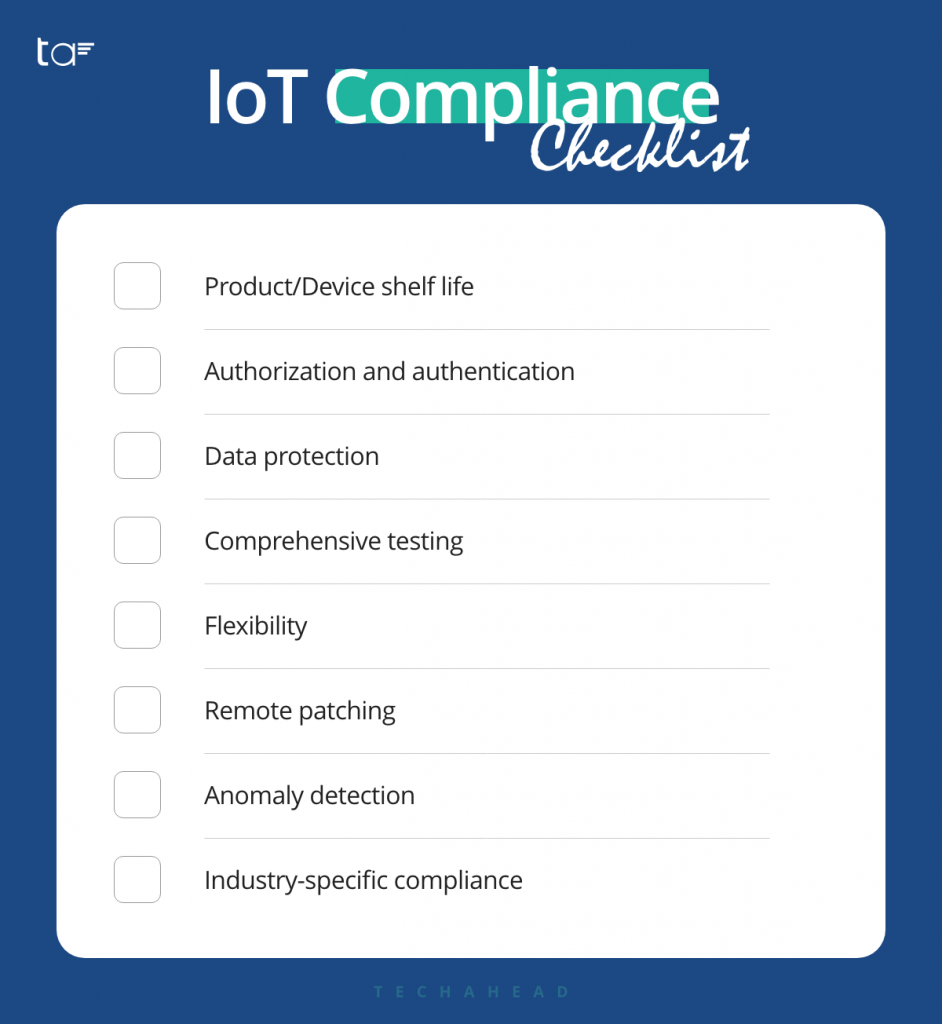
For instance, while drawing up the IoT compliance checklist, care must be taken to include the following factors:
Product /Device shelf life — Every product or device has a shelf life, which should ideally be declared at the time of its launch. Care must be taken to update or replace them, as the case may be for each of them. Ensuring compliance can prove to be more expensive for products or devices past serviceable life.
Authorization and authentication — Permission to access or update data in devices must be given only to those who need it absolutely. This becomes important specially in multi-user products for tracing security incidents.
Data protection —Decision must be taken during the design phase on what type of data is to be generated by the IoT system and how they should be stored. Collecting and gathering unnecessary data increases risk of compromise and drives expenses as well.
Comprehensive testing — IoT products and devices must be tested exhaustively for all security risks listed and all protocols and guidelines to be adhered. Depending upon the IoT system and monument, compliance to additional guidelines by government or industry bodies might need to be incorporated.
Flexibility – It is essential to ensure that the IoT framework is flexible enough to incorporate new tools and guidelines.
Remote patching— Recalling products or services is expensive. So, they must be designed to allow remote patching in case any issue arises.
Anomaly detection – The IoT platform must be capable of identifying unusual patterns in data or unusual behavior by the devices so that intrusions can be detected in time.
Industry-specific compliance – As discussed earlier, some industries have more stringent guidelines for operations. These must be part of the compliance checklist.
IoT systems should be audited the way any IT system is audited. The standardized procedure for the organization should be used by the auditors. Auditing ensures that the standard protocols for developing applications is met.
TechAhead’s approach to compliance
We at TechAhead believe in developing solutions that have compliance built into them by design. Our team of IoT solutions experts use established benchmarks to do this. What we have discussed here is just a glimpse into our approach to IoT compliance. When our experts work on an IoT solution for you, we ensure that the solution has a robust IoT security framework and it is 100% compliant.
Summary
According to a 2018 DigiCert survey, all the companies that struggle to implement IoT security compliance faced at least one IoT security incident. Data breaches can result in an estimated loss of USD 42.9 billion to the top 10 Tech companies on FTSE 100 and Nasdaq 100 annually. To mitigate these losses, it is imperative to implement IoT compliance by design. People, processes, devices, technologies and applications making up the IoT ecosystem must be compliant. Every IoT management team must have at least one person who is responsible for ensuring that compliances are met.
Securing IoT systems is crucial because IoT devices can prove to be the weak gateway to whole networks. A smart light bulb or camera can be an easy way for hackers to break into the network. IoT systems should not compromise the confidentiality, integrity and availability of information systems. Studies have also revealed that occurrence of IT security incidents is directly proportional to an organization’s access to IT security expertise.
To ensure compliance, the first step must be to analyze the product or service would be operating in for risks. After the first version of the product or service is ready, tests must be conducted to ensure that compliance checklist is followed. Periodic audits must be performed to ensure continued compliance. Every product or device has a shelf life. The must be retired at the end of it so that they don’t make the whole system vulnerable to security attacks.
Protocols for authorization, authentication, data protection, comprehensive testing need to be put in place. The IoT platform must be able to identify unusual patterns in data or unusual behavior by devices so that potential intrusions can be detected in time. The product or service must also be designed for remote patching so that future updates can be made without having to recall them. IoT systems should also be audited the way any IT system is.
Source: techaheadcorp