Why Security Spending in Cloud App Development Will Grow by 24% in 2024?
Recent forecasts by Gartner highlight a projected 24% growth in spending on cloud security for 2024, pointing toward a pivotal shift in financial priorities.
Wondering why there is a significant focus on cloud security spending?
As organizations were shifting to a cloud-first approach throughout the last decade, cloud application developers were met with an evolving array of cyber threats and cloud vulnerabilities. It is owing to this observation and realization that the role of cloud application development services in ensuring data privacy and cloud security has become more crucial than ever. Let’s dig deeper to see what’s happening in the cloud security segment.
What’s Driving the Expenditure on Security in Cloud Application Development?
By 2027, it’s predicted that 70% of enterprises will adopt industry cloud platforms to scale their business operations. This surge in cloud adoption not only underscores the technology’s growing value but also points to the need for more robust security investments to protect these environments. Here are some other reasons why cloud application developers and owners are investing more in security.
Evolving Cyber Threats
As technology advances, so do cybercriminals’ methods, as evidenced by rising threats like malware injection, cryptojacking, denial of service (DoS), etc. Especially within cloud environments, sophisticated attacks can snowball. As per IBM, over 82% of malicious breaches involve data stored in cloud applications. This is because cloud infrastructures often involve complex networks with vast amounts of data across various services and applications. This complexity can create more points of vulnerability that can be exploited.
Cloud Misconfiguration Leading to a Massive Data Breach for Toyota Motors
In June 2023, Toyota Motors revealed a data breach impacting around 260,000 customers due to a misconfigured cloud environment. Having been undetected from February 2015 to May 2023, this breach exposed in-vehicle device IDs, map updates, and related metadata.
Even though no “highly sensitive information” was leaked, this data breach is still considered to be an eye-opening incident that highlights the severe risks posed by simple configuration errors that leave room for malicious actors.
Rising Data Privacy Concerns
In recent years, many high-profile data breaches have exposed millions of personal records, like the Snowflake attack, where over half a billion customers had their records leaked on the dark web. Such incidents have significantly impacted company reputations, demanding them to focus on strengthening their cloud security measures. This has pressed for increased spending on cloud security.
Stricter Regulatory Compliance Requirements
The increasing emphasis on regulatory requirements such as GDPR, HIPAA, and PCI-DSS enforces stringent data protection protocols. Non-compliance with these regulations can result in substantial fines and reputational damage, necessitating companies to invest more in securing their cloud environments. Ensuring compliance with all can significantly drive up spending on cloud security.
Intricacies of Securing the Cloud
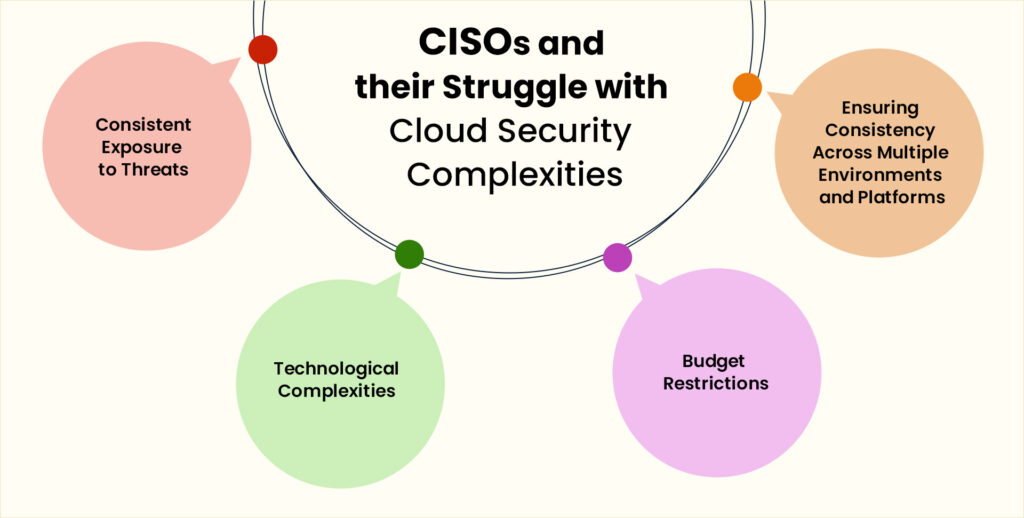
Given the vulnerabilities of cloud-based applications, cloud application security presents certain challenges for CISOs (chief information security officers).
Consistent Exposure to Threats
Cloud-based applications are more vulnerable because they’re accessible from virtually anywhere. This increases the risk of both insider threats and external breaches. Even employees or contractors with access to cloud-based resources can misuse or mishandle this data. Moreover, as cloud application developers regularly update these applications, there’s an increased chance of unauthorized access.
Technological Complexities
Cloud applications are often containerized (divided into smaller units called containers). While this enhances efficiency by allowing multiple containers to run on a single system, it also introduces unique vulnerabilities. The complexity of configuring these containers securely can lead to multiple errors. At larger scales, this complexity can challenge cloud application developers, increasing the hassle of putting security measures in place.
Budget Restrictions
With expanding cloud infrastructure, securing enough budget for security enhancements can be a considerable challenge. Security funding often contends with other expenses, such as product research, sales & marketing, etc.
Consistency Across Multiple Environments and Platforms
Ensuring unified security across multiple cloud environments and hybrid systems/applications is another significant challenge in cloud application development. Each cloud environment operates with distinct tools and configurations, making it tougher to apply security policies universally.
Effective Strategies for Enhanced Cloud Security
Several solutions are surfacing as organizations now prioritize security in cloud application development. These solutions span two primary areas: strategic cloud security budgeting and cost-effective security initiatives. Let’s explore them in detail.
Strategic Cloud Security Budgeting
Implementing strategic budgeting is intuitively the first step to optimizing spending on security in cloud application development.
- Your cloud application developers should begin with a clear understanding of the organization’s most sensitive assets on the could. Once you identify where vulnerabilities are, you can allocate funds to more critical areas where security is needed the most. This prioritization reduces wasteful spending.
- Another way to aid smart budgeting is to regularly assess cloud risks, ensuring that funds flow toward measures and technologies that counter evolving threats.
- You can also integrate automated threat detection technologies in your cloud application development process. By leveraging advanced AI/ML algorithms, they can scan for anomalies and potential threats in real time. With such consistent surveillance, automation prevents costly breaches, justifying the initially higher upfront investment over the long run.
Advanced Cloud Security Initiatives
In response to evolving cyber threats, seeking advanced security initiatives has become imperative. One such example is the Zero Trust model. This model treats all access requests—whether from inside or outside the network—with the same level of scrutiny. By enforcing strict verification through this model, cloud application developers can ensure tightened security for all applications.
Cloud Native Application Protection Platforms (CNAPPs) are another emerging cloud security tools that offer comprehensive security across all services. CNAPPs offer an integrated set of tools that facilitate unified security management by enhancing visibility into all cloud resources. Security teams can easily detect misconfigurations, suspicious activities, and unauthorized changes across cloud environments.
What Lies Ahead?
An increasing emphasis on cloud security is fundamental to protecting digital assets. As we look ahead, this emphasis will only grow because organizations today are shifting from the traditional cloud-first approach to a more refined, secure cloud-smart approach. The latter combines existing, on-premises infrastructure with only relevant cloud capabilities to enhance overall performance. By keeping sensitive data on-premises, you can have full control over its security and compliance while still leveraging the cloud for less critical data and workloads. In the end, it’s all about making well-informed decisions that guarantee that your data is secure.
This shift has also called for cloud application developers to embed robust security features into applications right from the design phase. It not only enhances the functionality of cloud-based applications but also fortifies them against evolving threats.
Source: suntecindia